How to deploy a cluster with Red Hat OpenShift Service on AWS using the console UI
This resource will take you through the steps to deploy a Red Hat OpenShift® Service on AWS cluster using the OpenShift® Cluster Manager (OCM) user interface (UI).
What will you learn?
- How to deploy a ROSA cluster using the console interface
What do you need before starting?
- Met all prerequisites
Now we’ll look at the second option for deploying your cluster: using the console user interface.
Deploying a cluster with the UI
Follow these steps to deploy a ROSA cluster using the OCM UI.
Deployment flow
The overall flow that we will follow is below. Step 1 only needs to be performed the first time you are deploying into an AWS account. Step 2 only needs to be performed the first time you are using the user interface. So for each successive cluster of the same y-stream version, you would just create the cluster.
- Create the account wide roles and policies
- Associate your AWS account with your Red Hat account
- Create and link OCM role
- Create and link User role
- Create the cluster
Create account-wide roles
NOTE: If you already have account roles (possibly from an earlier deployment) then skip this step. You will see that the UI will detect your existing roles after you select an associated AWS account.
If this is the first time you are deploying ROSA in this account and have not yet created the account roles, then create the account-wide roles and policies, including Operator policies.
In your terminal run the following command to create the account-wide roles:
rosa create account-roles --mode auto --yes
You will see an output like the following:
I: Creating roles using 'arn:aws:iam::000000000000:user/rosa-user'
I: Created role 'ManagedOpenShift-ControlPlane-Role' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-ControlPlane-Role'
I: Created role 'ManagedOpenShift-Worker-Role' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-Worker-Role'
I: Created role 'ManagedOpenShift-Support-Role' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-Support-Role'
I: Created role 'ManagedOpenShift-Installer-Role' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-Installer-Role'
I: Created policy with ARN 'arn:aws:iam::000000000000:policy/ManagedOpenShift-openshift-machine-api-aws-cloud-credentials'
I: Created policy with ARN 'arn:aws:iam::000000000000:policy/ManagedOpenShift-openshift-cloud-credential-operator-cloud-crede'
I: Created policy with ARN 'arn:aws:iam::000000000000:policy/ManagedOpenShift-openshift-image-registry-installer-cloud-creden'
I: Created policy with ARN 'arn:aws:iam::000000000000:policy/ManagedOpenShift-openshift-ingress-operator-cloud-credentials'
I: Created policy with ARN 'arn:aws:iam::000000000000:policy/ManagedOpenShift-openshift-cluster-csi-drivers-ebs-cloud-credent'
I: To create a cluster with these roles, run the following command:
rosa create cluster --stsAssociate your AWS account with your Red Hat account
NOTE: If you have already associated AWS accounts that you want to use, please skip this step.
The next step is to tell OCM what is/are your AWS account(s) that you want to use for deploying ROSA into.
Open OCM by visiting https://console.redhat.com/openshift and log in to your Red Hat account.
Click on the "Create Cluster" button.
Then in the ROSA row (about midway down the page, under "Managed services") click on the "Create Cluster" button.
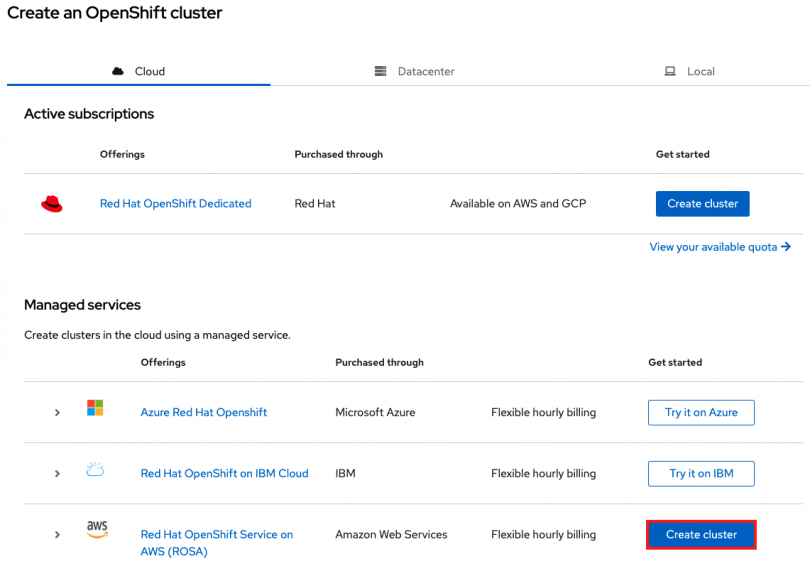
Check the box stating that you have read and completed all the prerequisites.
Then click the dropbox under "Associated AWS account". You may see that there are no associated accounts. This is expected since we have not associated any AWS accounts yet. Click on the box that says "Associate AWS account."
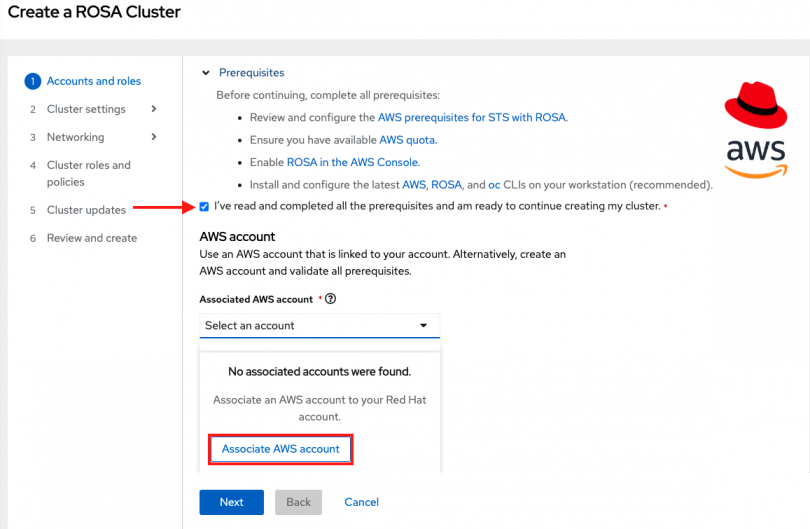
A pop up window will open instructing you to download the ROSA CLI, AWS CLI, and to log into your Red Hat account. If you have been following this learning path, we already did this in a previous section, so just click "Next".
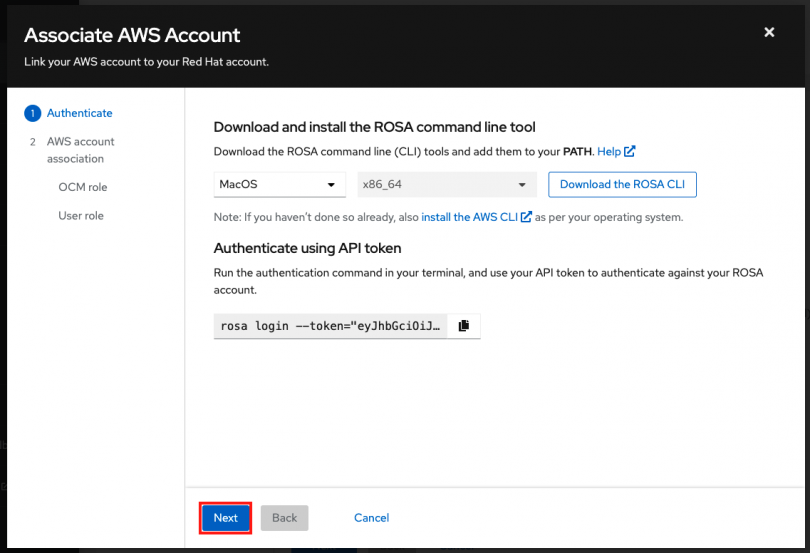
On the next page you will see the commands to create the OCM role for the level of permissions that this role will have. You can create:
- Basic OCM role: Allows OCM to have read-only access to the account in order to check if the roles and policies that are required by ROSA are present before creating a cluster. You will need to manually create the required roles, policies and OIDC provider using the CLI.
- Admin OCM role: Grants OCM additional permissions in order to create the required roles, policies, and OIDC provider for ROSA. Using this makes the deployment of a ROSA cluster quicker since OCM will be able to create the required resources for you avoiding the need for you to manually create them.
To read more about these roles, please visit the OpenShift Cluster Manager roles and permissions section of the documentation.
For the purposes of this workshop, we'll use the Admin OCM role since we want the simplest and quickest approach.
Create and associate an OCM role
You can copy the command for the Admin OCM role from that window which will launch interactive mode. Or for simplicity switch to your terminal and execute:
rosa create ocm-role --mode auto --admin --yes
I: Creating ocm role
I: Creating role using 'arn:aws:iam::000000000000:user/rosa-user'
I: Created role 'ManagedOpenShift-OCM-Role-12561000' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-OCM-Role-12561000'
I: Linking OCM role
I: Successfully linked role-arn 'arn:aws:iam::000000000000:role/ManagedOpenShift-OCM-Role-12561000' with organization account '1MpZfntsZeUdjWHg7XRgP000000'This will create the OCM roles for you and associate them with your Red Hat account.
NOTE: As an alternative, you can define --mode manual if you'd prefer to execute the AWS CLI commands yourself. The AWS commands will be outputted to the CLI and the relevant JSON files will be created in the current directory. Also make sure to link the role as well which is the last command output. Also, if you insist on creating a Basic OCM role, then just remove --admin from the command above.
Then, click "Next".
Create an OCM User role
As defined in the documentation, the user role needs to be created so that the ROSA service can verify your AWS identity. This role has no permissions, and it is only used to create a trust relationship between the installer account and your OCM role resources.
Run the following to create the User Role and to link it to your Red Hat account.
rosa create user-role --mode auto --yes
You will see a response like:
I: Creating User role
I: Creating ocm user role using 'arn:aws:iam::000000000000:user/rosa-user'
I: Created role 'ManagedOpenShift-User-rosa-user-Role' with ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-User-rosa-user-Role'
I: Linking User role
I: Successfully linked role ARN 'arn:aws:iam::000000000000:role/ManagedOpenShift-User-rosa-user-Role' with account '1rbOQez0z5j1YolInhcXY000000'
Click “Ok.”
Confirm successful association
You will be brought back to the original window in which you should see your AWS account that you associated above in the drop down. If you see your account there, it was successful.
Select the account.
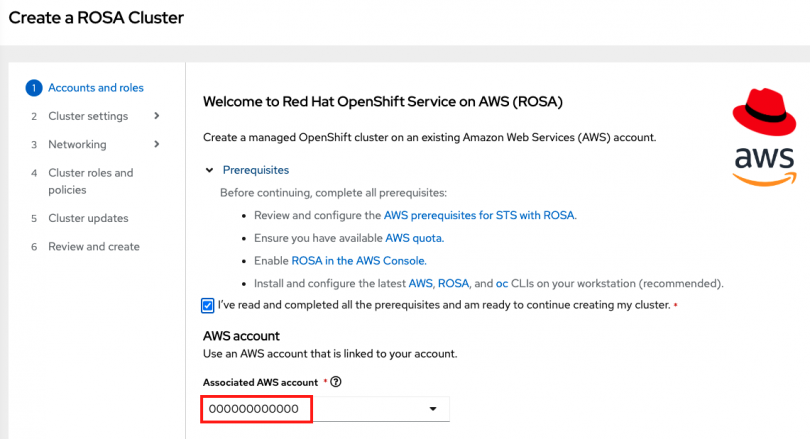
You will then see the account role ARNs (created earlier) populated below. Then click “Next”.
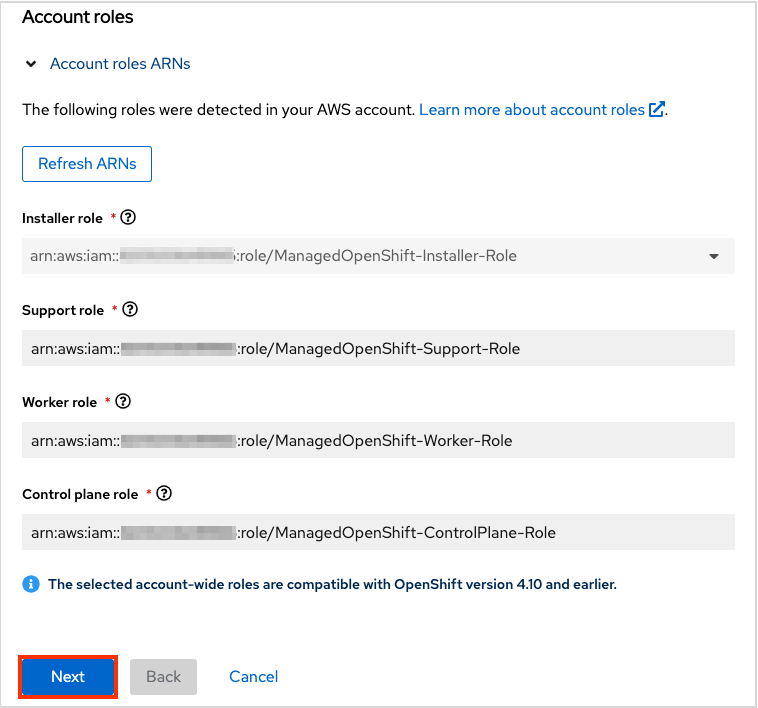
Create the cluster
For the purposes of this learning path, make the following selections.
Cluster settings
Details:
- Cluster name: <pick a name>
- Version: <select latest version>
- Region: <select desired region>
- Availability: Single zone
- Enable user workload monitoring: leave checked
- Enable additional etcd encryption: leave unchecked
- Encrypt persistent volumes with customer keys: leave unchecked
Click "Next".
Machine pool (leave the defaults which are):
- Compute node instance type: m5.xlarge - 4 vCPU 16 GiB RAM
- Enable autoscaling: unchecked
- Compute node count: 2
- Leave node labels blank
Click "Next".
Networking
Configuration - Leave all default values
Click "Next".
CIDR ranges - Leave all default values
Click "Next".
Cluster roles and policies
For the purposes of this workshop leave "Auto" selected and it will make the cluster deployment process simpler and quicker.
NOTE: If you selected a Basic OCM role earlier you can only use manual mode and you must manually create the operator roles and OIDC provider. See "For Basic OCM roles only" section below after you've completed the "Cluster updates" section and started the cluster creation.
Cluster updates
Leave all the default options.
Review and create
Review the content for the cluster configuration and click "Create cluster".
Monitor installation progress
Stay at the current page to monitor the installation progress.
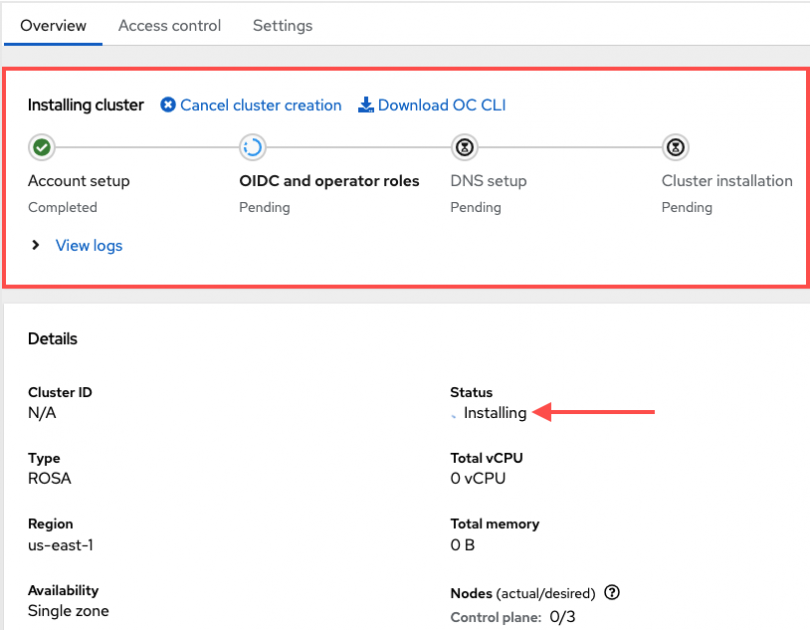
For Basic OCM role only
NOTE: If you created an Admin OCM role as directed above please ignore this section since OCM will create the role for you.
Create operator roles
If you created a Basic OCM Role earlier, you will need to manually create 2 more elements before the cluster installation can continue.
Operator roles
OIDC provider
NOTE: To understand what these do, please see the “What is STS?” resource.
There will be a pop up window that will show you the commands to run.
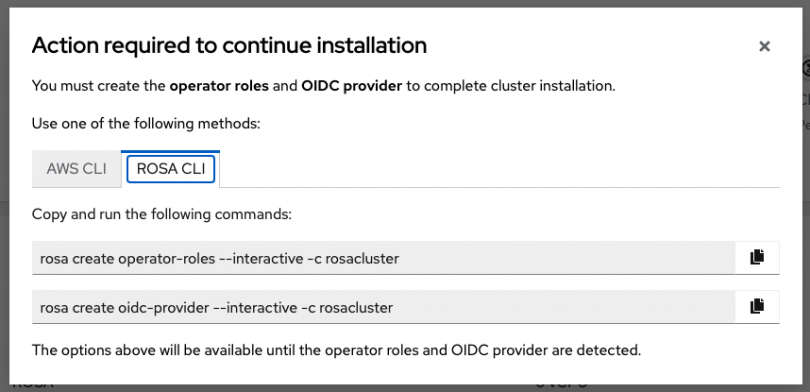
In your terminal, you may run the commands from the window which will launch interactive mode. For simplicity, though, run the following to create the Operator roles:
rosa create operator-roles --mode auto --cluster <cluster-name> --yes
You will see a response like:
I: Creating roles using 'arn:aws:iam::000000000000:user/rosauser'
I: Created role 'rosacluster-b736-openshift-ingress-operator-cloud-credentials' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-ingress-operator-cloud-credentials'
I: Created role 'rosacluster-b736-openshift-cluster-csi-drivers-ebs-cloud-credent' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-cluster-csi-drivers-ebs-cloud-credent'
I: Created role 'rosacluster-b736-openshift-cloud-network-config-controller-cloud' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-cloud-network-config-controller-cloud'
I: Created role 'rosacluster-b736-openshift-machine-api-aws-cloud-credentials' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-machine-api-aws-cloud-credentials'
I: Created role 'rosacluster-b736-openshift-cloud-credential-operator-cloud-crede' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-cloud-credential-operator-cloud-crede'
I: Created role 'rosacluster-b736-openshift-image-registry-installer-cloud-creden' with ARN 'arn:aws:iam::000000000000:role/rosacluster-b736-openshift-image-registry-installer-cloud-creden'Create OIDC provider
In your terminal run the following to create the Operator roles:
rosa create oidc-provider --mode auto --cluster <cluster-name> --yes
You will see a response like:
I: Creating OIDC provider using 'arn:aws:iam::000000000000:user/rosauser'
I: Created OIDC provider with ARN 'arn:aws:iam::000000000000:oidc-provider/rh-oidc.s3.us-east-1.amazonaws.com/1tt4kvrr2kha2rgs8gjfvf0000000000'
You are now ready to move on to the next resource, where you’ll learn how to create an admin user.
- Want to experiment within a cluster yourself? Dive into our Developer Sandbox with a 30-day no-cost trial, where you can practice building within OpenShift.
