Testing frameworks for images built via Lightspeed image builder
Now that the image is built, it’s time to look at testing frameworks, compliance monitoring, and reporting. In this resource, we will cover how to monitor the system’s compliance using Lightspeed (formerly Insights) Compliance. We’ll then compare that monitoring approach to using custom-built testing frameworks leveraging tools such as Amazon Web Services (AWS) Security Hub.
What will you learn?
- Conducting Lightspeed compliance monitoring, policies, and reporting
- Creating custom testing framework using AWS Security Hub
What do you need before starting?
- Cloud service provider account credentials
- Red Hat account
Compliance monitoring
The choice to use the “PCI-DSS” profile was not an arbitrary one. Due to limitations with AWS Security Hub, we were not able to run scans for the “CIS” profile. This is because Amazon only recognizes images built with AWS when attempting to scan and report compliance for “CIS”.
To get started with Lightspeed compliance, we need to make sure we have the correct permissions to access the feature. We need either the Lightspeed compliance viewer role or the administrator role. We can check our access by clicking on the user icon in the top right corner of the screen and then selecting the My User Access option.
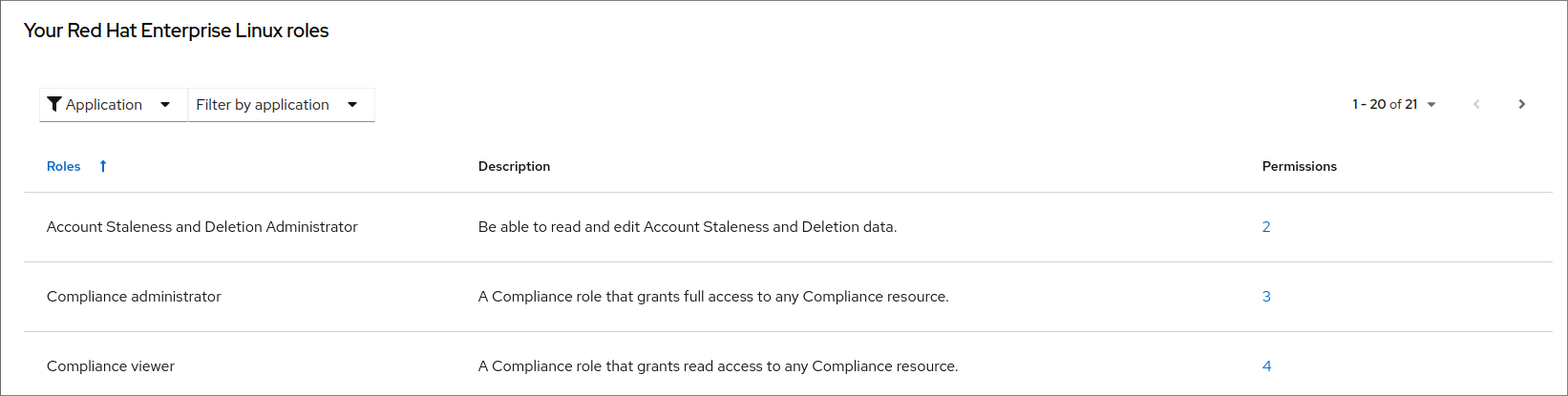
You should see the “Compliance administrator” and the “Compliance viewer” roles. If you do not see these options, you should contact your organization administrator to arrange access.
Register the instance
For ease of use, It is highly recommended that users pre-register the image with Lightspeed during the image creation. We can pre-register the image in the “Create Image Wizard” using Activation Keys in Lightspeed image builder. Please see Getting started with activation keys on the Hybrid Cloud Console for further guidance.
Additionally, you will need to ensure that you have Simple Content Access (SCA) enabled on your account. This provides the simplest experience to ensure subscriptions are automatically usable on the system. The default setting is "enabled" for new accounts. For older accounts that may not have this option enabled, you may need to contact your company's org admin for the Red Hat account to enable SCA.
Create the policy and attach it
We now need to create and assign a policy and attach it to the instance from Lightspeed compliance in the console. To do this, navigate to SCAP policies.
If available, you can select an existing policy, or create a new policy. Depending on your organization, some profiles may have already been created by the org admin or another user. For the purpose of this demo, we will create a new one.
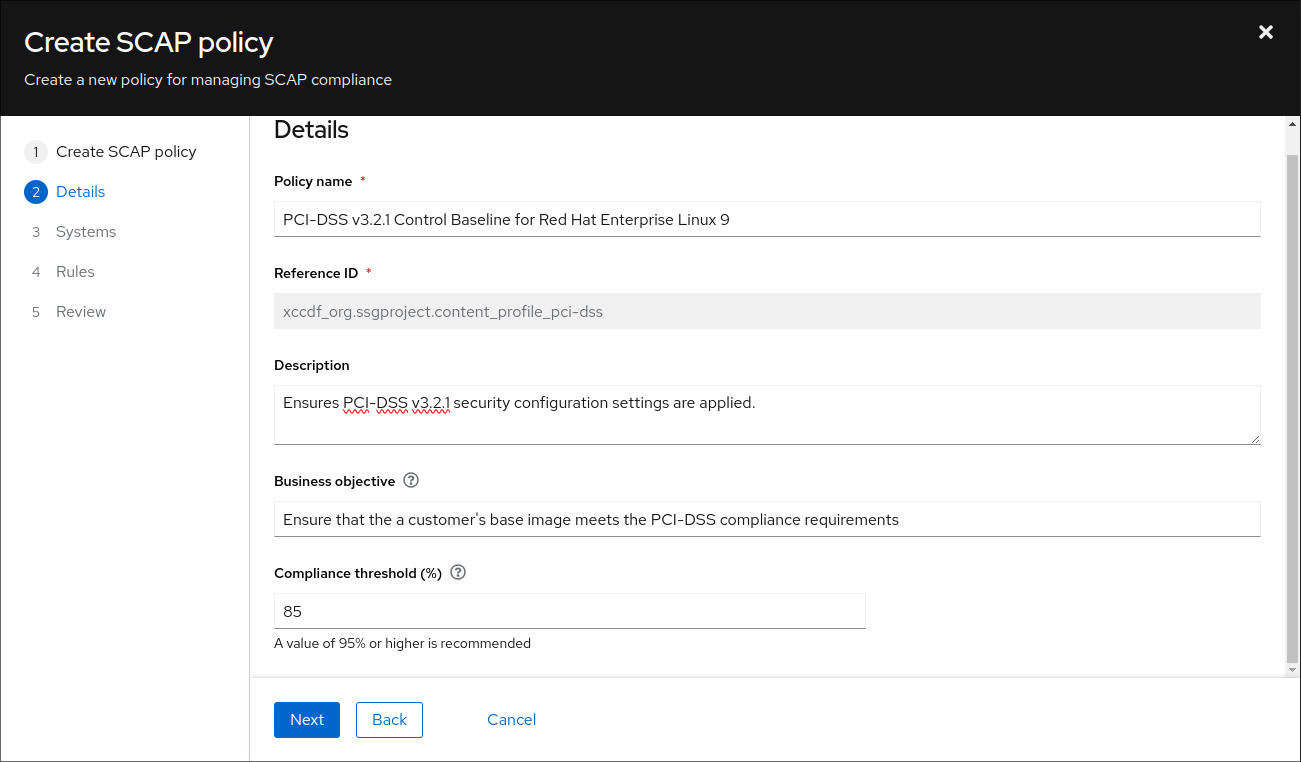
For the policy, we will select Red Hat Enterprise Linux® 9 for the operating system. Next, we need to provide a description of the policy, the business objective, and compliance threshold. For the business objective, we are trying to ensure that a customer’s base image meets the PCI-DSS compliance standards. As such, we’ll use that as the objective.
The compliance threshold describes the margin of error with which we are satisfied to consider the system as compliant with the standard. We will choose 95% for this demonstration, since there are still some remediation steps that need to be run manually in order to get a 100% compliant image built with Lightspeed image builder.
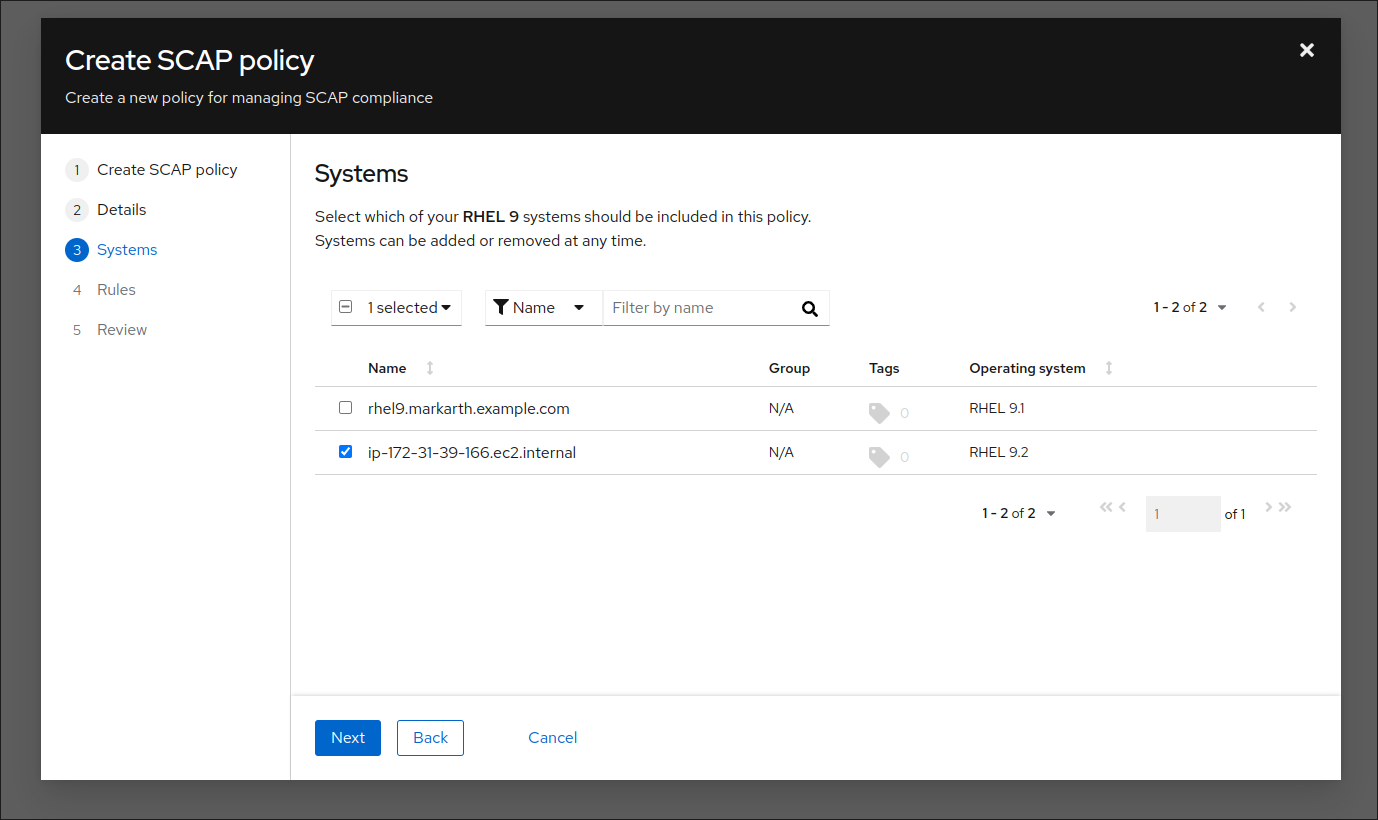
We then need to register our system with the policy we are creating in Lightspeed compliance; otherwise, running the compliance report generation will fail. We can select the system from the dropdown. The name of the system should match the IP address of the EC2 instance we have created and launched.
We will leave the default rules for the policy since tailoring profiles in Lightspeed image builder is not yet available at the time of writing, April 2024. Finally, we can review the policy and create it. We should now see the created policy in the list of SCAP policies.
Run the scan
We are now ready to run a scan and generate a report on the instance. To do so, we can run the following command:
```bash
sudo insights-client –compliance
```View the report
We can now navigate to the reports page under Lightspeed compliance:
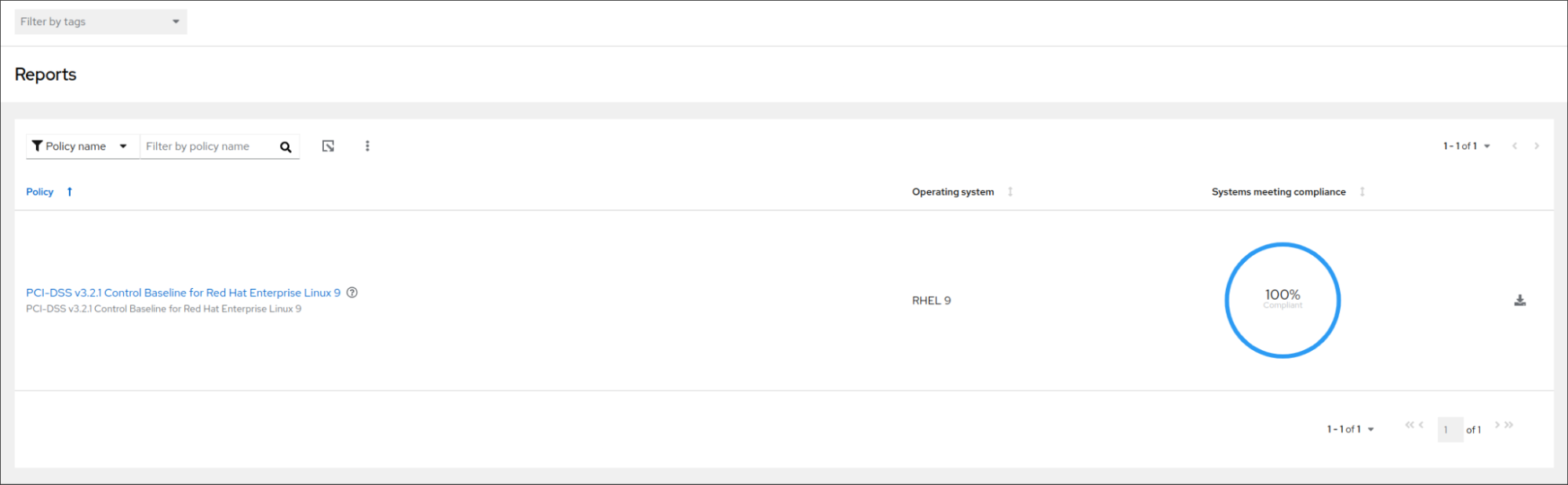
We can see in the above screenshot that the image is 100% compliant since it met the compliance threshold of 95%. We can click on the report, get additional information, and see which rules are non-compliant in order to perform manual intervention.
