Creating a custom testing framework using AWS Security Hub
In this section, we will be building a custom testing framework using Amazon Web Services (AWS) Security Hub, which enables users to monitor the security and compliance of instances in AWS. Before we start, please note that AWS Security Hub and AWS config must be enabled prior to running this script, or else the dashboard won’t be populated.
What will you learn?
- Creating custom testing framework using AWS Security Hub
What do you need before starting?
- Cloud service provider account credentials
- Red Hat account
Custom testing framework using AWS Security Hub
Next, let’s compare that monitoring approach to using custom-built testing frameworks leveraging tools such as AWS Security Hub. To test an AWS AMI created by Red Hat® Lightspeed (Insights) image builder, we’re going to build out the following testing framework below.
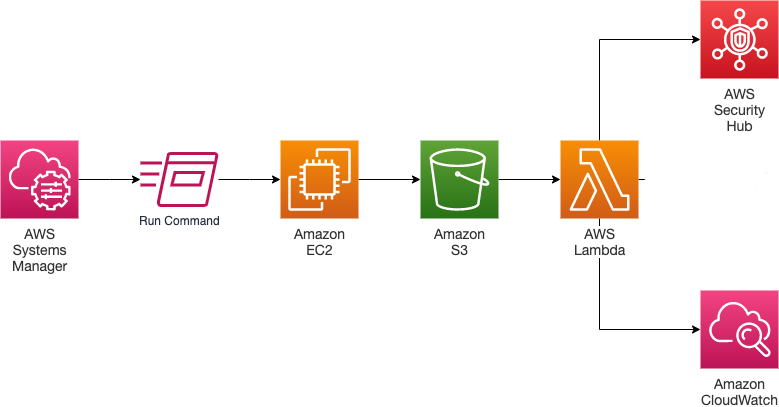
The framework operates by raising a RHEL AMI on an EC2 instance, then AWS Systems Manager (SSM) is deployed to run a set of commands that will:
- Install the OpenSCAP scanning utility
- Perform the vulnerability scan to see if it’s PCI-DSS compliant
- Publish the results into both an XML and html file, and push them to an S3 bucket
Once S3 detects that an object has been pushed to the designated bucket, it will then trigger a lambda function to scan the bucket for the XML file. Once it has found the XML, the lambda function will pull it from S3, process the file, and push the results to AWS Security Hub. At that point, the results of the scan should be visible in the AWS Security Hub dashboard. The cloudwatch component of the framework is there purely for monitoring and troubleshooting purposes.
Now, access the AWS web console and locate your AMI in the EC2 section. Click on the Images tab -> AMI -> Private Images. Locate the AMI ID and sub that value into the Terraform code found at https://github.com/oezeakachi/open_scap_aws to raise the framework. Once the build is complete, go to the AWS Security Hub in the AWS web console and check the PCI dashboard to see how compliant the AMI is.
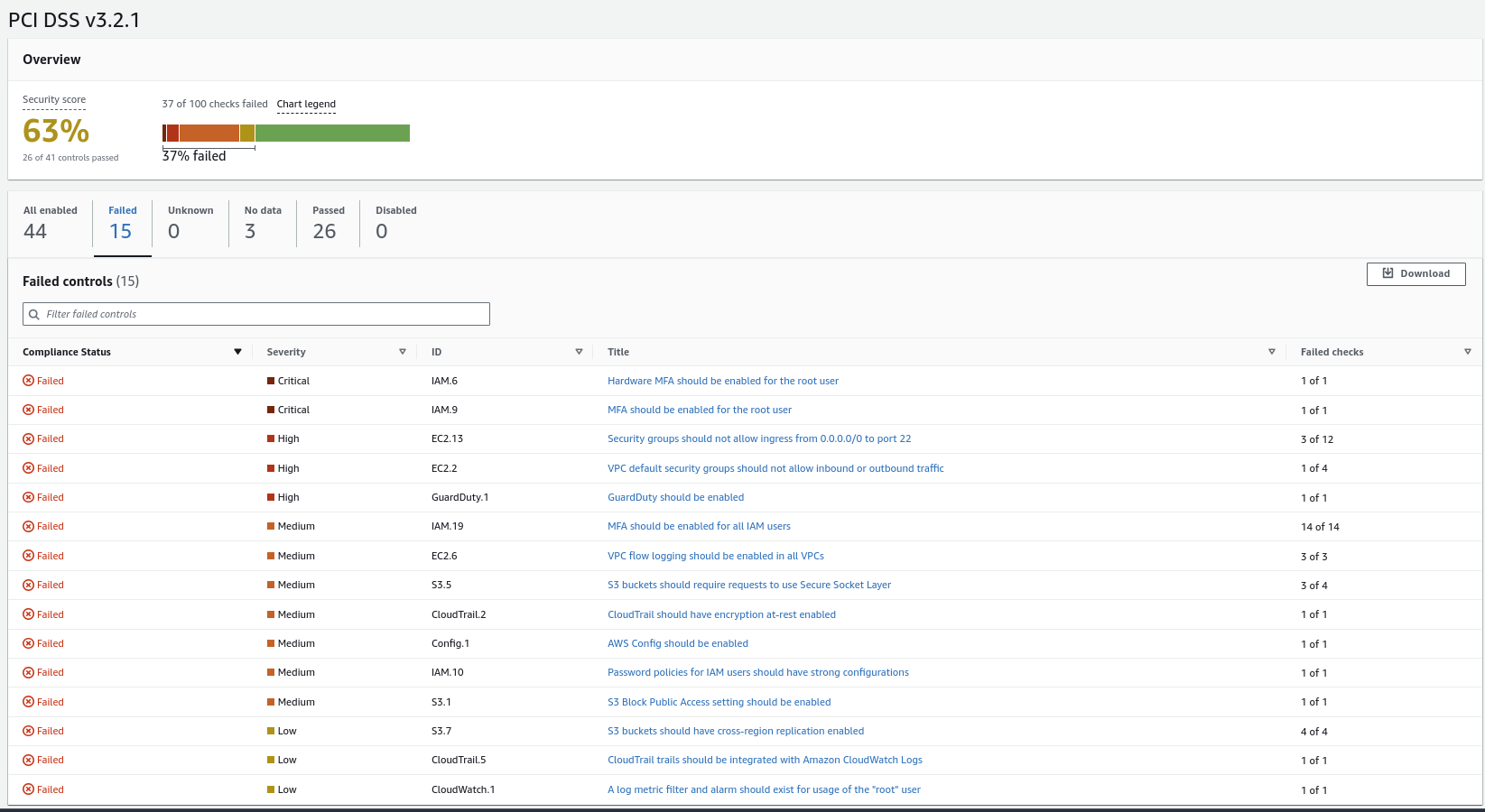
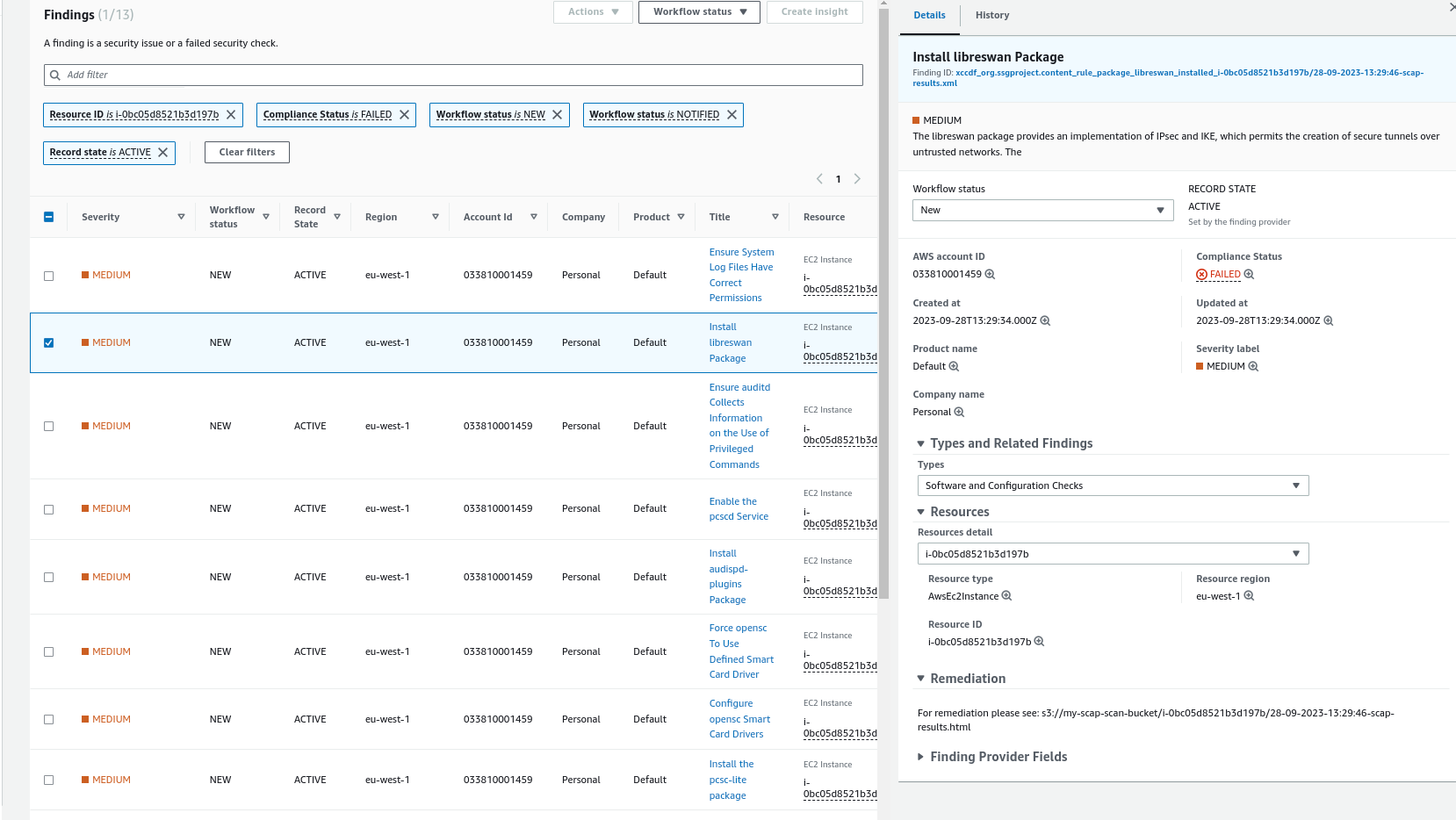
Further information can be found by clicking on the Findings tab and searching for the EC2 instance that’s using the AMI via its ID.
In conclusion, the custom OpenSCAP testing framework generates a thorough vulnerability report that can be viewed as an HTML file in an S3 bucket. The framework can also push the results to a dashboard in AWS Security Hub (which is pre-configured to display results for a set list of security standards specifically for AWS-based images). However, a custom framework has the additional overhead of implementation and maintenance.
On the other hand, Lightspeed succeeds in all the areas where the custom frameworks fail. It offers a clear and concise scanning process and a simple way of viewing the subsequent results. In addition to this, the tool is not limited to scanning images from a single cloud service and can scan any subscribed image in all formats (AWS, Azure, on-premise, etc).
