Securely exposing an application on a private ROSA cluser with an AWS Network Load Balancer
This content is authored by Red Hat experts, but has not yet been tested on every supported configuration.
Continuation of Securely exposing an application on a private ROSA cluser with an AWS Network Load Balancer
These instructions go through setting up an additional VPC as part of the overall blog. If you already have a VPC that you would like to use, you can skip these instructions.
Looking at the overall architecture, this section will setup everything in the blue box.
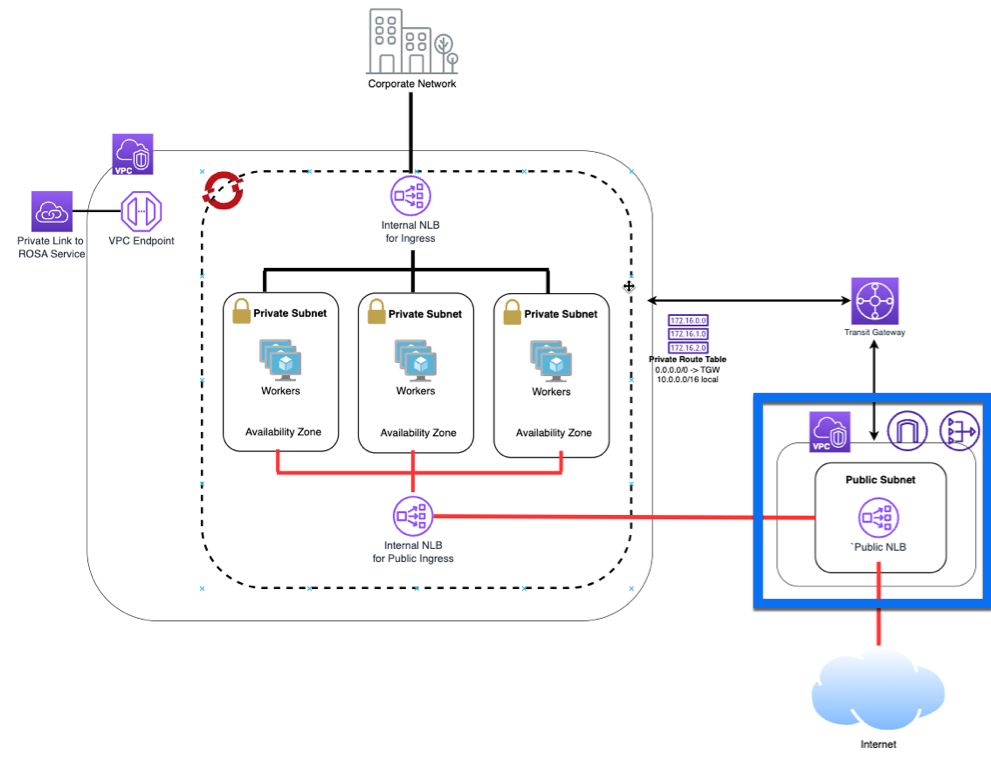
Create a public VPC
The VPC we will be creating will have a VPC with a private subnet, a public subnet where the Network Load Balancer will sit, an Internet Gateway and a Nat Gateway.
Set Environment Variables
This section also expects the ROSA_VPC_ID, ROSA_VPC_CIDR, ROSA_PRIVATE_R_TABLE_IDS, and ROSA_PRIVATE_SUBNET_IDS environment variables to be set which is done in the parent blog.
Create a VPC
Create a Public Subnet for the cluster to NAT egress traffic out of
Create a Private Subnet for a jump host
Create an Internet Gateway for NAT egress traffic
Create a Route Table for NAT egress traffic
Create a NAT Gateway for the Private network
Create a Route Table for the Private subnet to the NAT
Peer the ROSA VPC with the NLB VPC
note: this tutotial will use a classic peering connection, a transit gateway can also be used.
