Configuring Microsoft Entra ID to emit group names
This content is authored by Red Hat experts, but has not yet been tested on every supported configuration.
In this guide, we will configure an existing Microsoft Entra ID (formerly Azure Active Directory) identity provider to emit the group name instead of the group ID for optional group claims. This will allow you to reference group names in your role bindings instead of the group ID.
The ability to emit group names instead of group IDs is a preview feature made available by Microsoft and is subject to their terms and conditions around preview features of their services.
Prerequisites
Before we begin, ensure that you have properly configured Microsoft Entra ID as an identity provider in your cluster following the guide specific to your platform:
In addition, ensure that you have the necessary permissions to modify the Microsoft Entra ID app registration in the Azure Portal.
Microsoft Entra ID Free is not able to emit group names instead of group IDs.
Procedure
Login to the Microsoft Azure portal and navigate to the Microsoft Entra ID service, then click on the App registrations blade.
Locate your App registration and click on it.
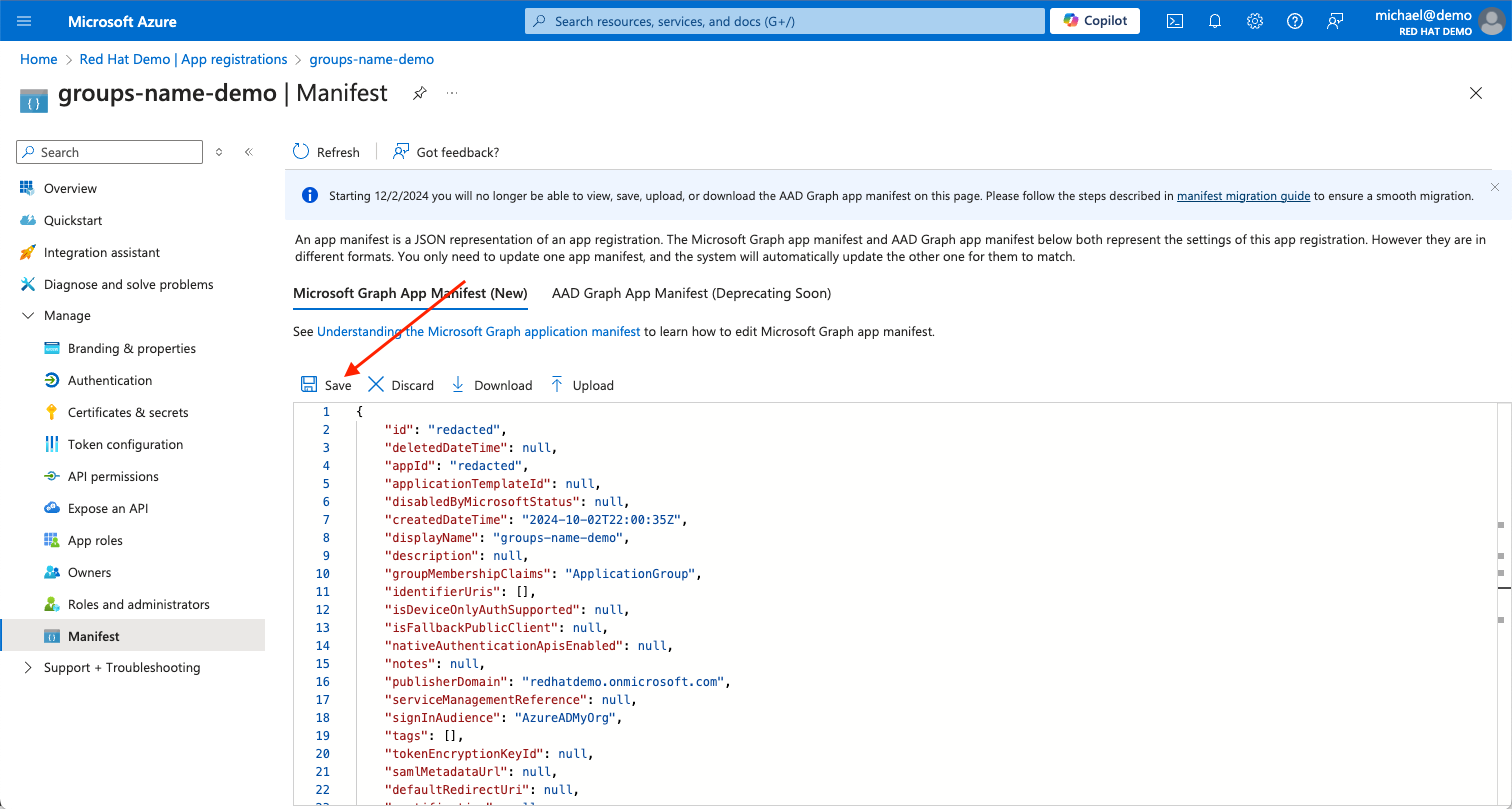
Expand the Manage sidebar menu, and click on the Manifest blade.
Download the Microsoft Graph App Manifest to keep as a backup, just in case.
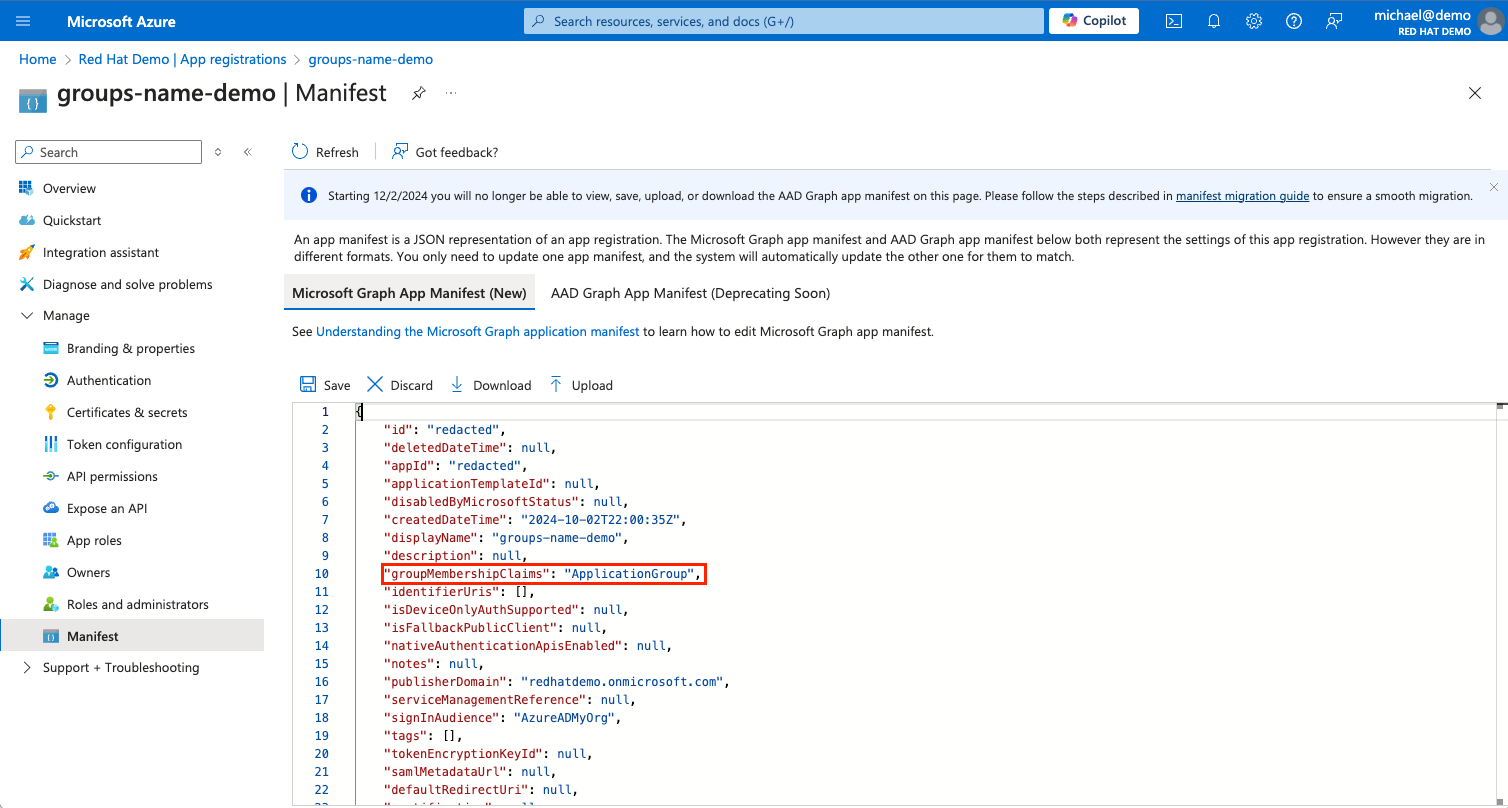
Locate the setting
groupMembershipClaimsand ensure it is set toApplicationGroup. This option includes only groups that are assigned to the application.Before changing this value, ensure that the groups you wish to include in your claims are attached to your Microsoft Entra ID application. Failure to do so may result in unexpected behavior including the removal of group memberships used for role bindings. For more information on how to add groups to your Microsoft Entra ID application, see the Microsoft documentation .
Locate the
groupsclaims under theoptionalClaimssection of the manifest. There should be three, one underaccessToken, one underidToken, and one undersaml2Token. Edit theadditionalPropertiesfield of thegroupsclaims for theidTokenonly. You will change theadditionalPropertiesfield to look like this:... "optionalClaims": { "idToken": [ { "name": "groups", "source": null, "essential": false, "additionalProperties": [ "sam_account_name", "cloud_displayname" ] } ], ...Save your changes.
If you are already logged into the OpenShift Web Console, logout. Once you are logged out of the cluster, log back in using the Microsoft Entra ID. You should now see group membership populated with group names instead of group IDs.
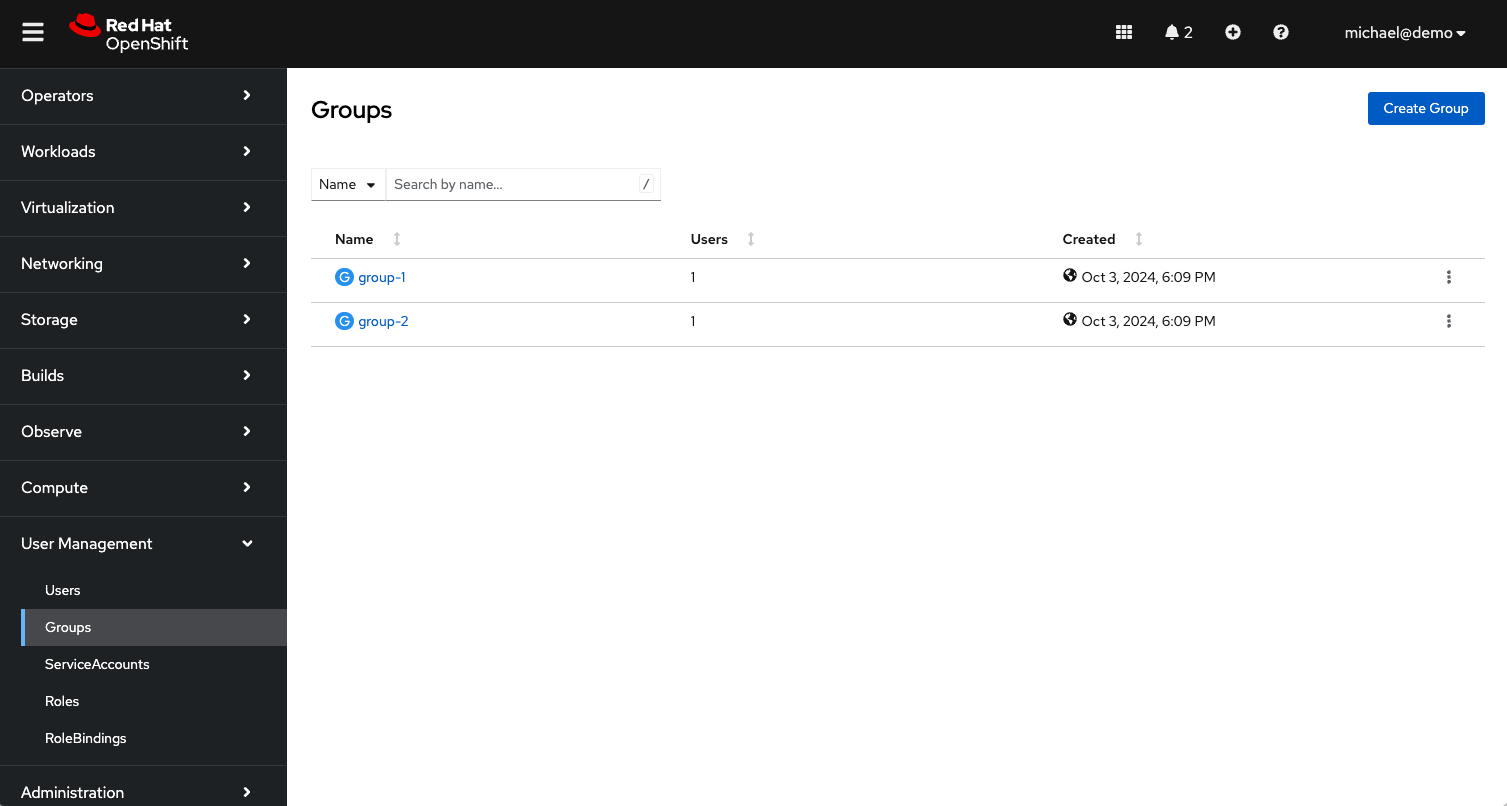
You can see these groups were synced from Microsoft Entra ID by running the
oc get groups -o yamlcommand. Your output will look something like this (note theoauth.openshift.ioannotations):apiVersion: v1 items: - apiVersion: user.openshift.io/v1 kind: Group metadata: annotations: oauth.openshift.io/generated: "true" oauth.openshift.io/idp.EntraID: synced name: group-1 users: - michael@demo - apiVersion: user.openshift.io/v1 kind: Group metadata: annotations: oauth.openshift.io/generated: "true" oauth.openshift.io/idp.EntraID: synced name: group-2 users: - michael@demo kind: List metadata: resourceVersion: ""
Congratulations! You are now able to reference your group names in role bindings instead of group IDs.
